Hashicorp Vault - Dynamic Secrets
What are dynamic secrets
In this post, we will discuss the topic of dynamic secrets. What are dynamic secrets then? A dynamic secret is a secret that is generated on demand as opposed to a static secret which is defined ahead of time. Let’s imagine you need a database password. Vault could then interact with the database engine and create a dynamic secret and associate it with a lease. Vault will then also automatically destroy the credentials when the lease expires.
Dynamic secrets can be created for various systems:
- Databases (MySQL, PostgreSQL, ….)
- Cloud providers (AWS, Azure….)
- SSH
- PKI
- …
In this post we will show the principles of dynamic secrets through AWS. The AWS secrets engine generates AWS access credentials dynamically based on IAM policies.
Enabling AWS secrets engine
First off, we need to enable the AWS secrets engine. This can be done through the CLI, the API or the UI. For simplicity sake, we will work through the UI here. Go to Secrets > Enable new engine and select the AWS secrets engine.
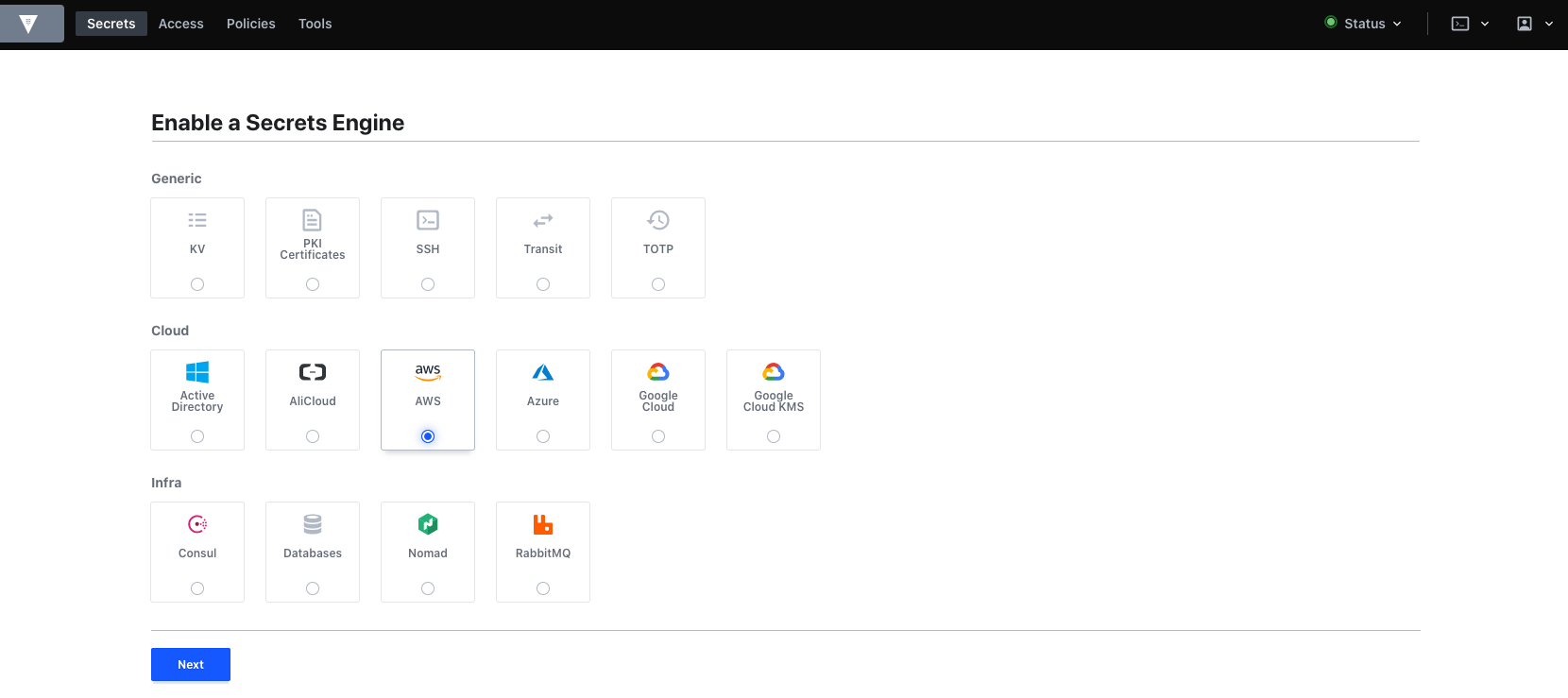
We will use the default path of AWS, which means our credentials will be stored under that path
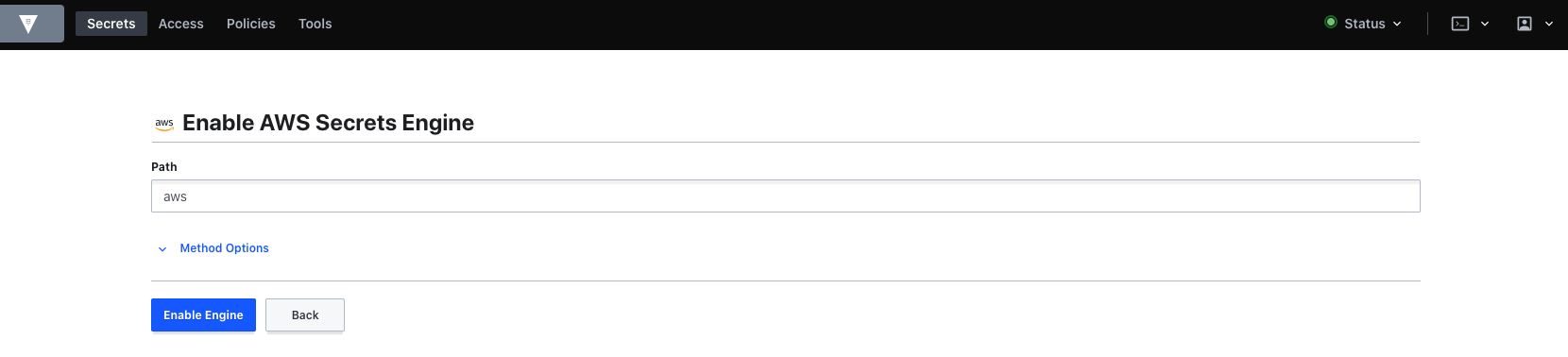
When the engine is enabled you will get a form to create a role.
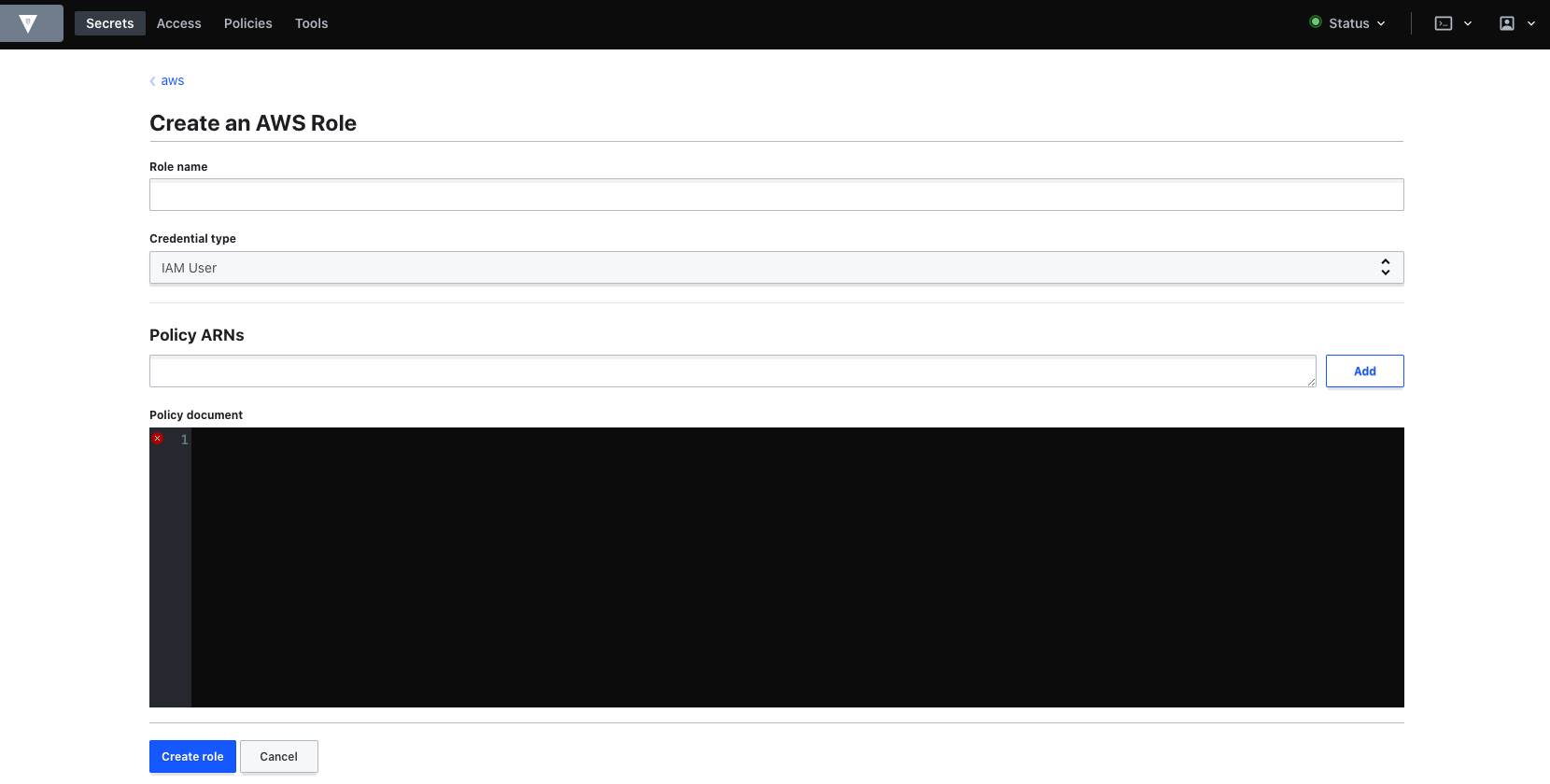
Define role in Vault and assign AWS policy
In terms of defining a role, we will need to give it a name. You will also notice (in below screenshot) that we need to specify a policy ARN or a policy document. Let’s head over to AWS console
In AWS, go to IAM and then go to Policies:
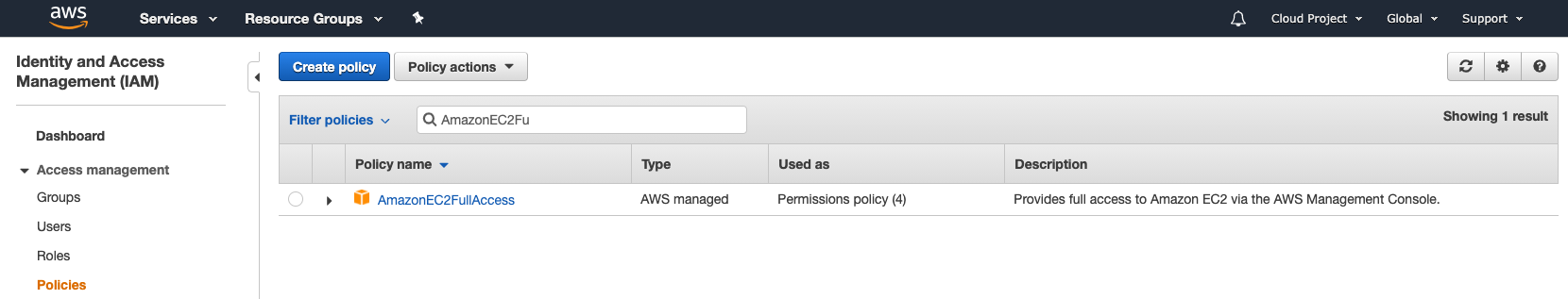
Copy the ARN (or the JSON)
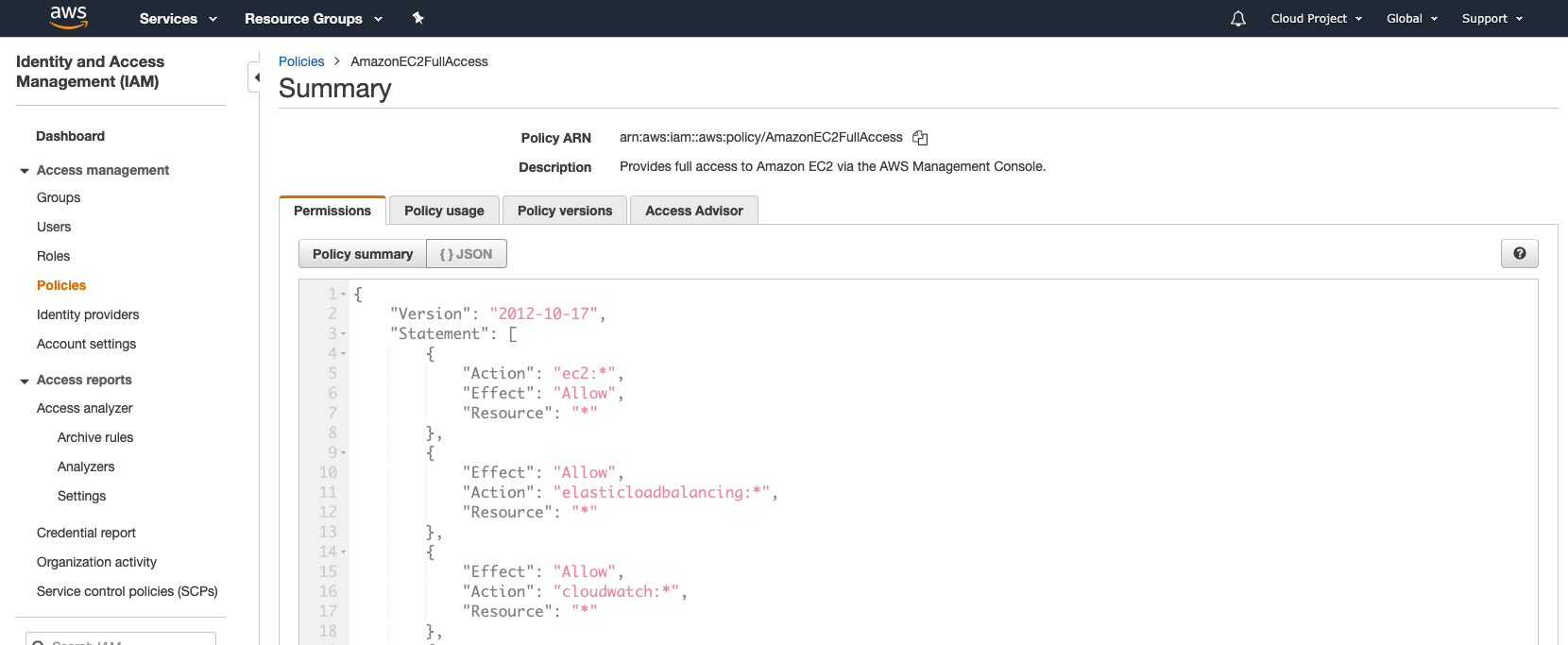
Go back to Vault to complete the configuration of the role:
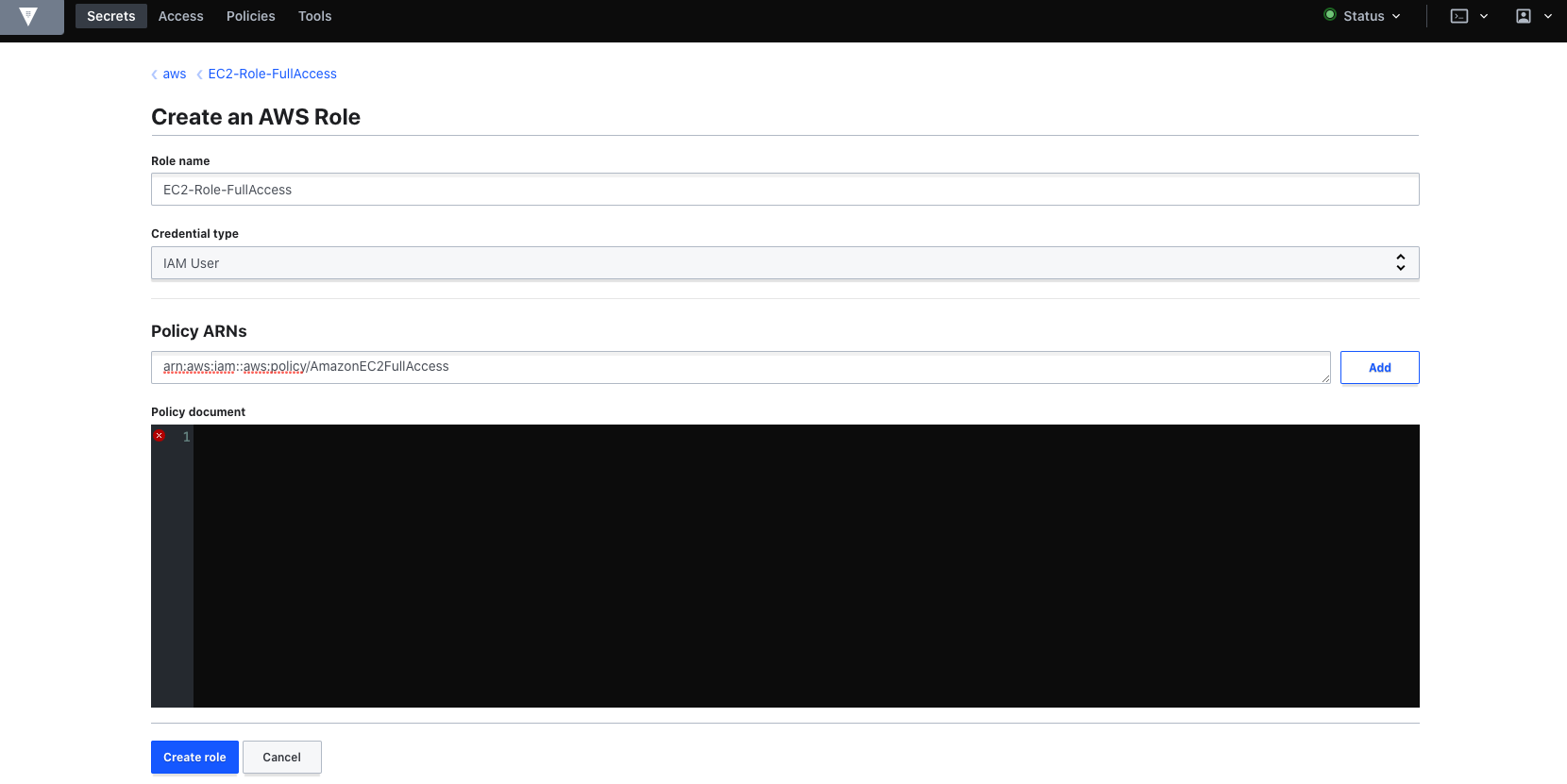
In this code we have opted to use the ARN but in case you copied the JSON policy, you should paste it in the policy document textbox.
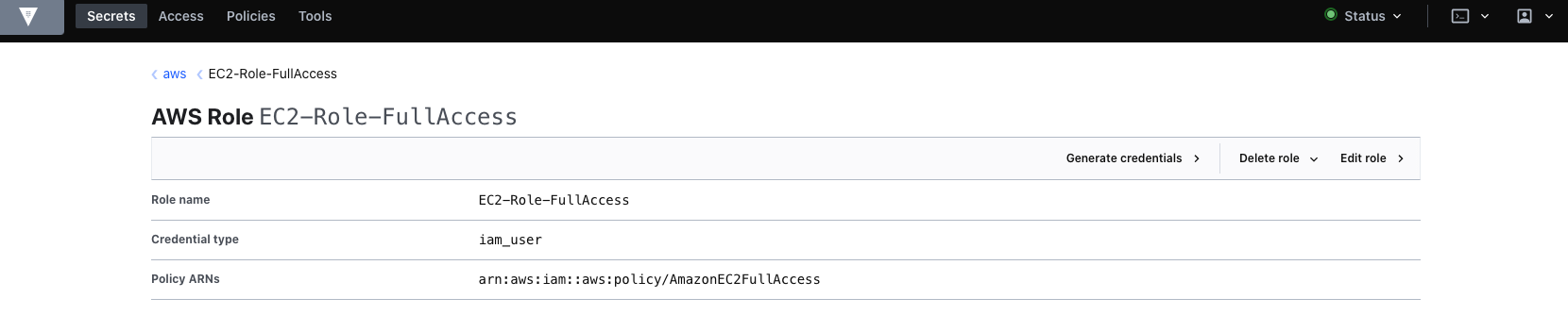
When finished, you will see we have a role available for use.
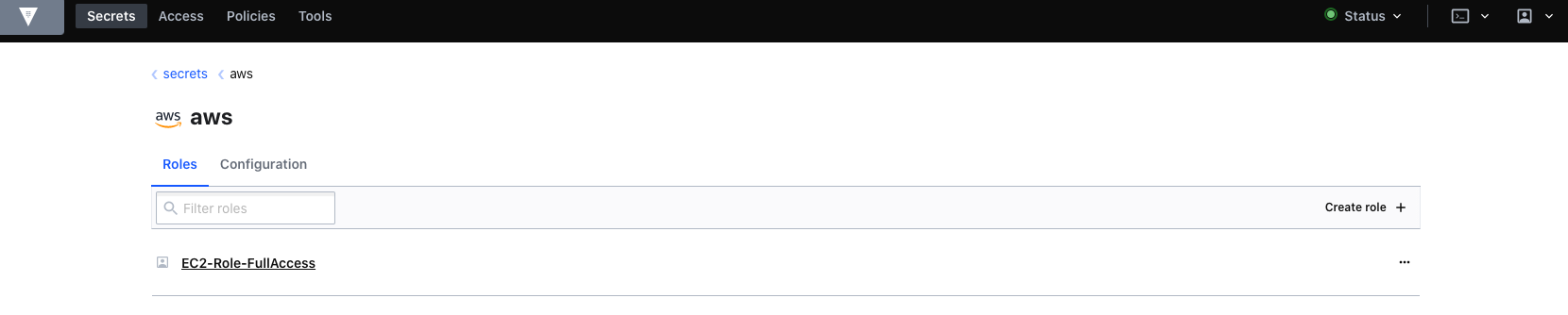
And some more details:
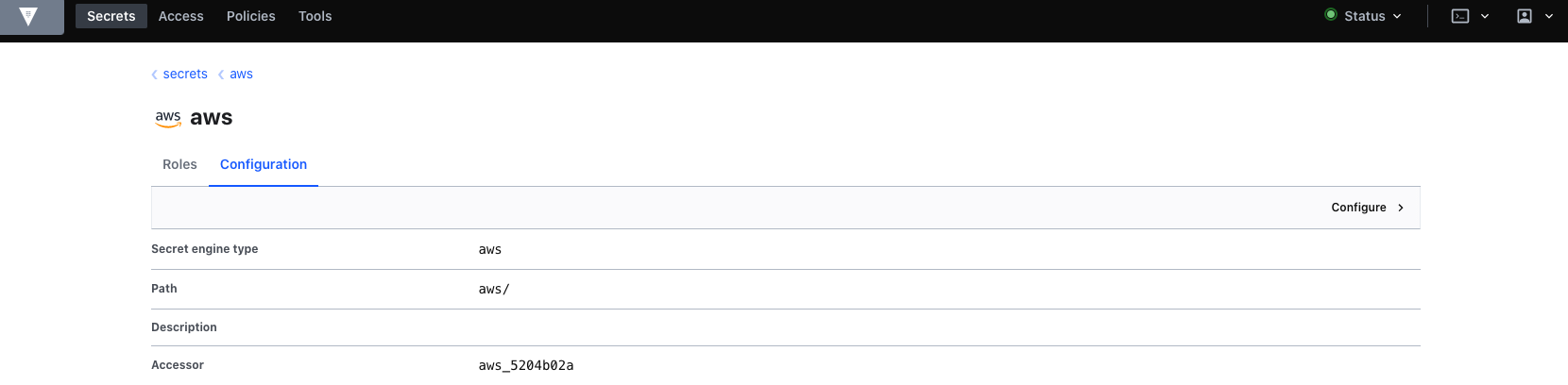
Configure Vault with AWS user
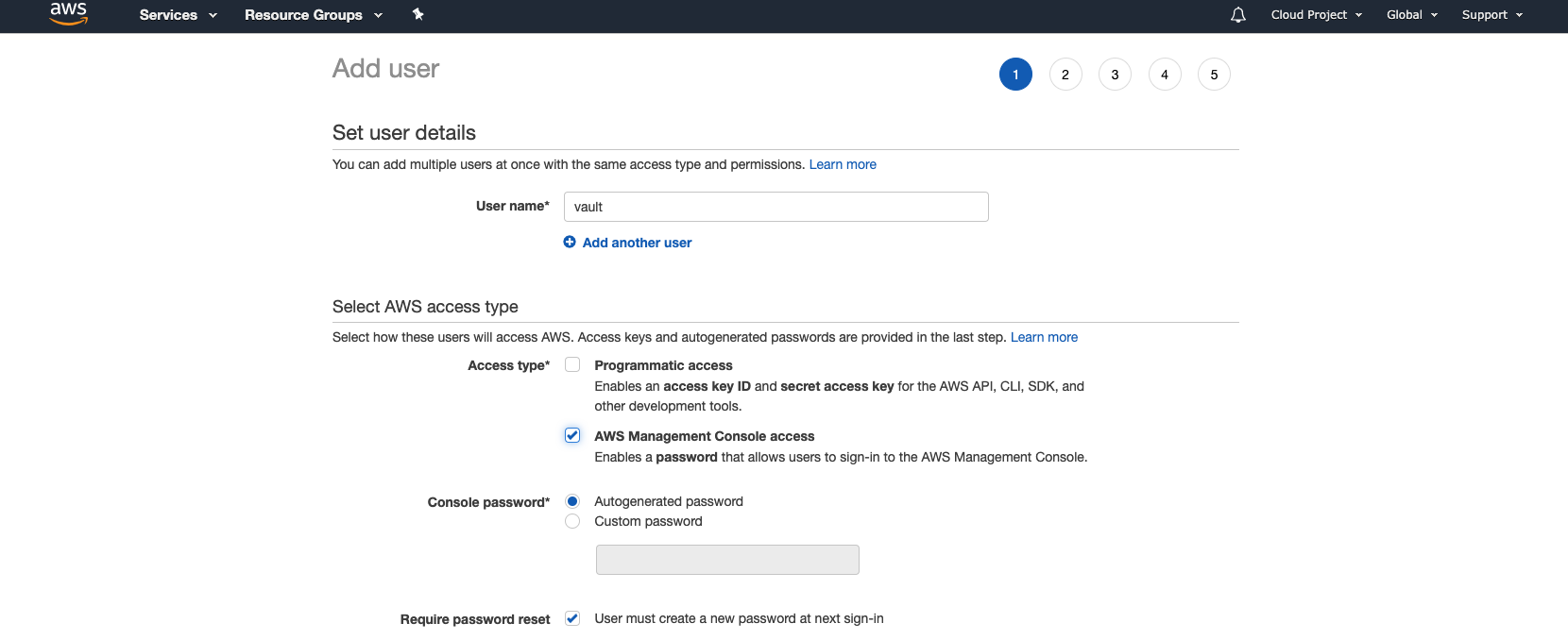
Next, we need to add an AWS user to Vault. This user will need to have permissions. In below screenshot, I gave full admin access which is something that should not be done. I just took the easiest approach to safe some time. I’m lazy :-)
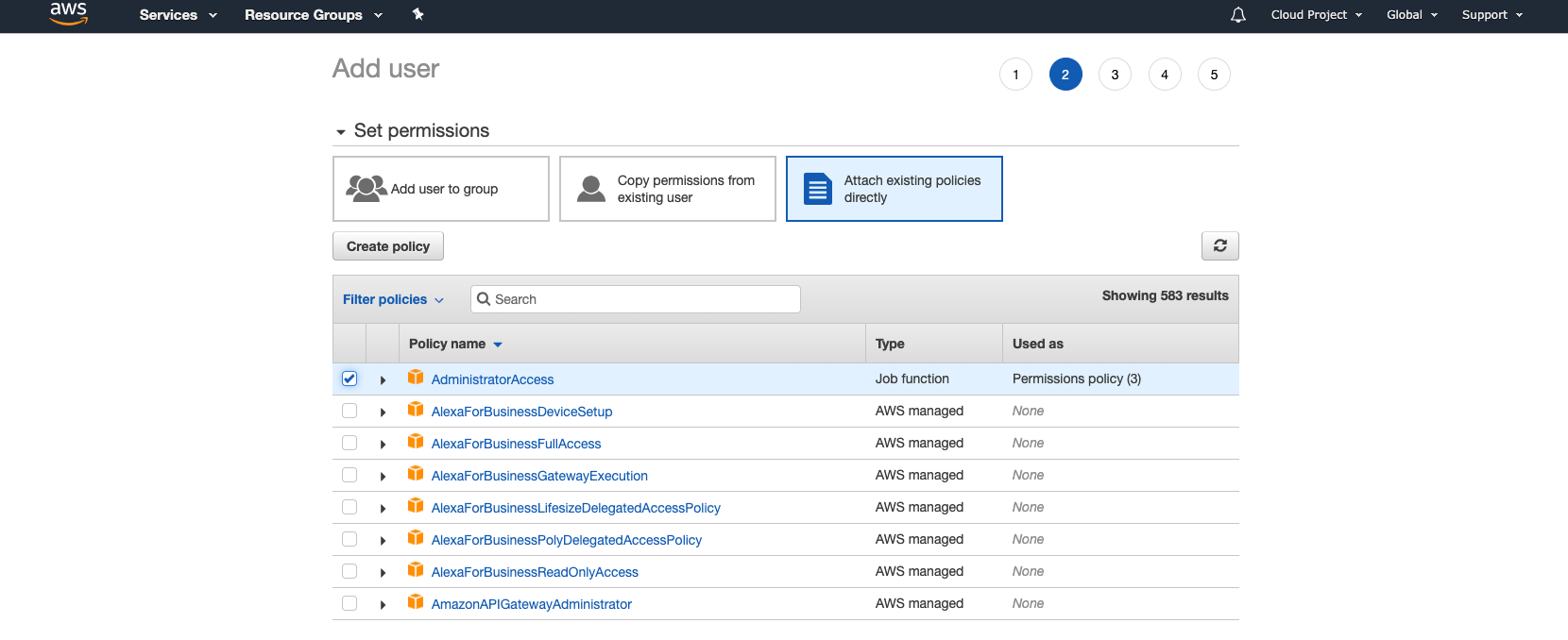
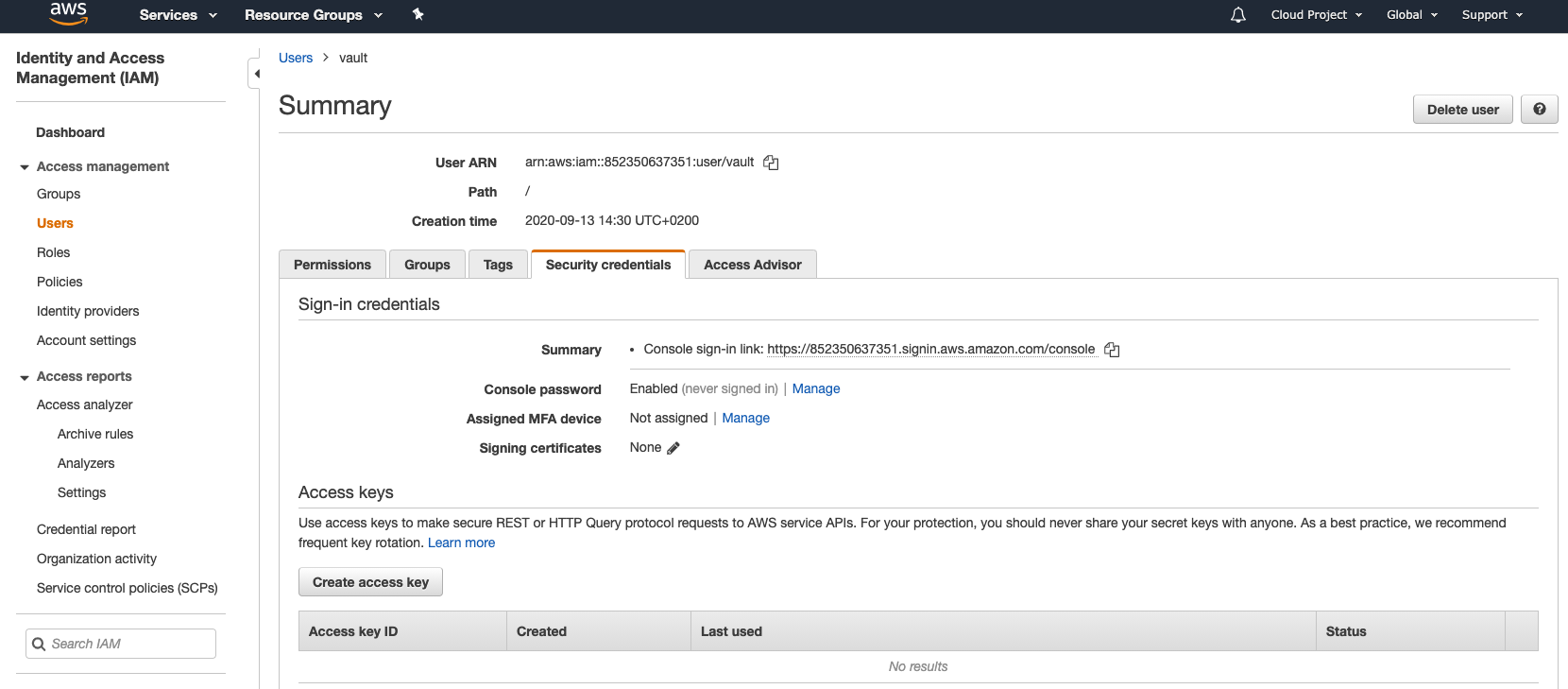
Take note of the security credentials. You will need them later when configuring Vault.
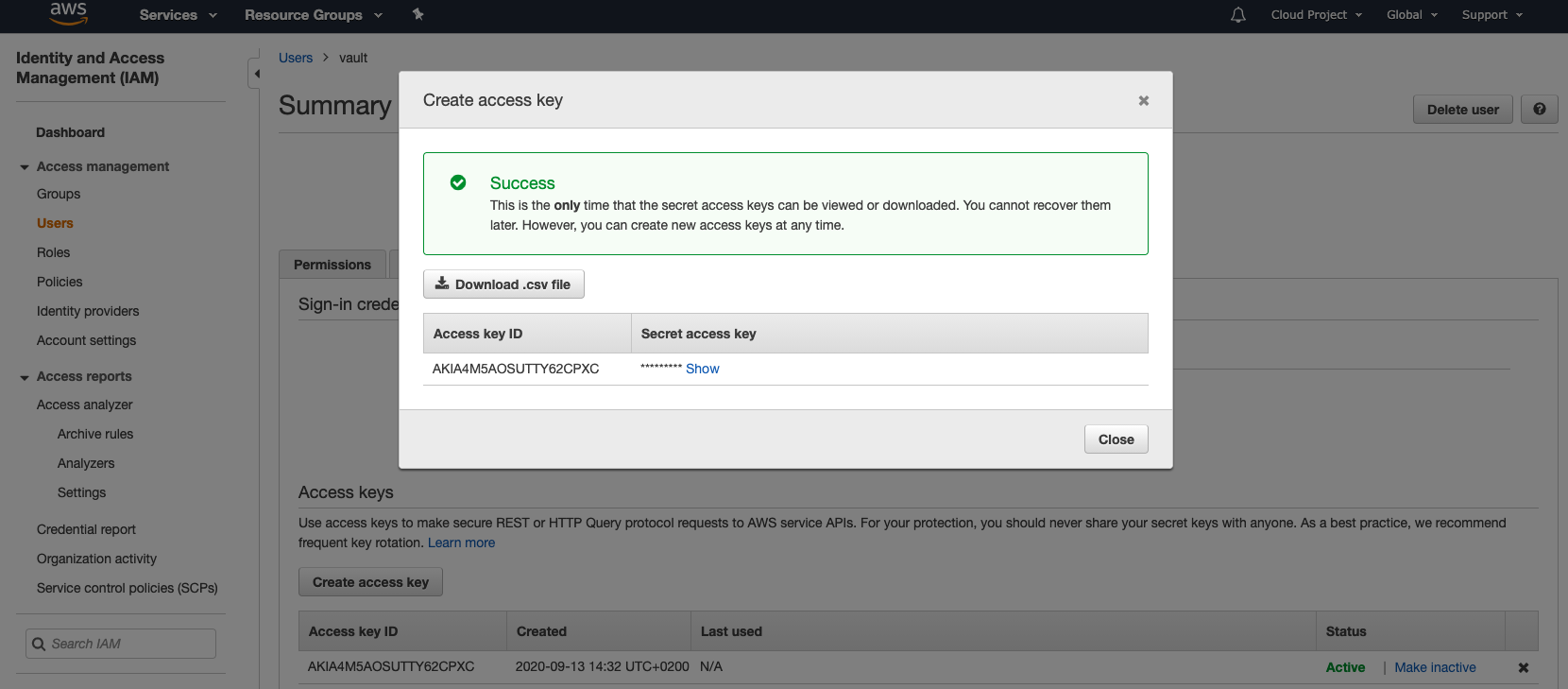
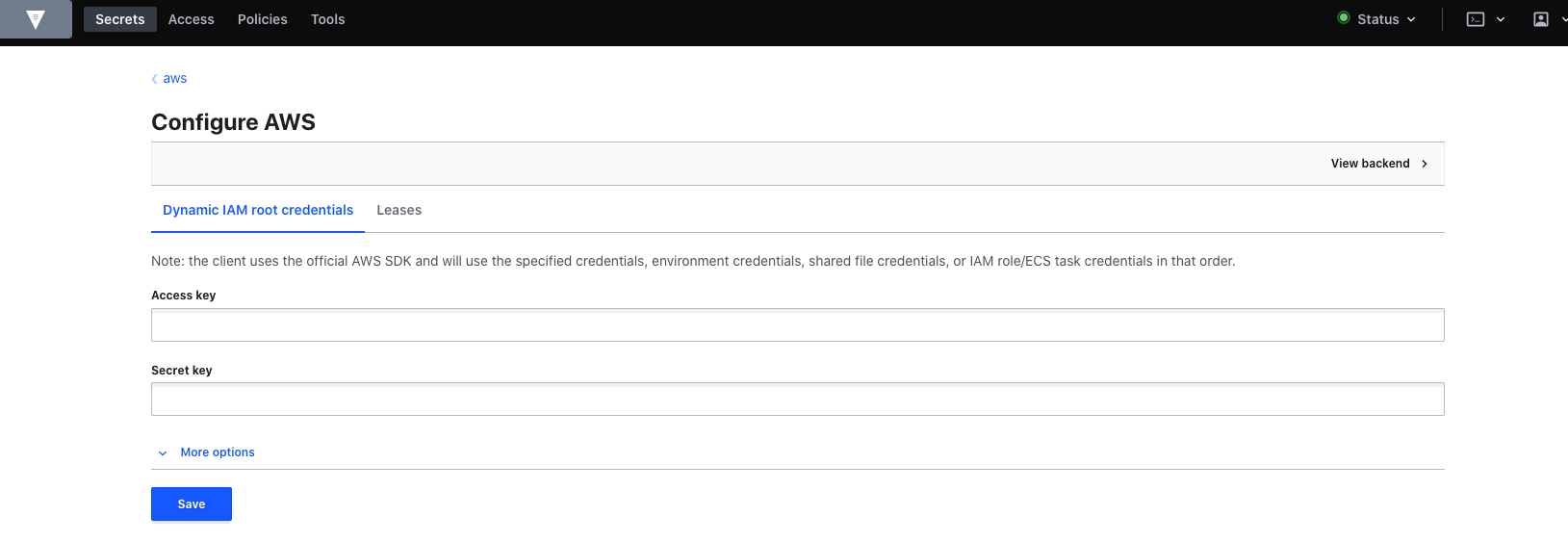
Next, go back to Vault > Secrets. Click on the aws path, then select Configuration and finally click on Configure > Dynamic IAM Root credentials. Add the access key and secret key.
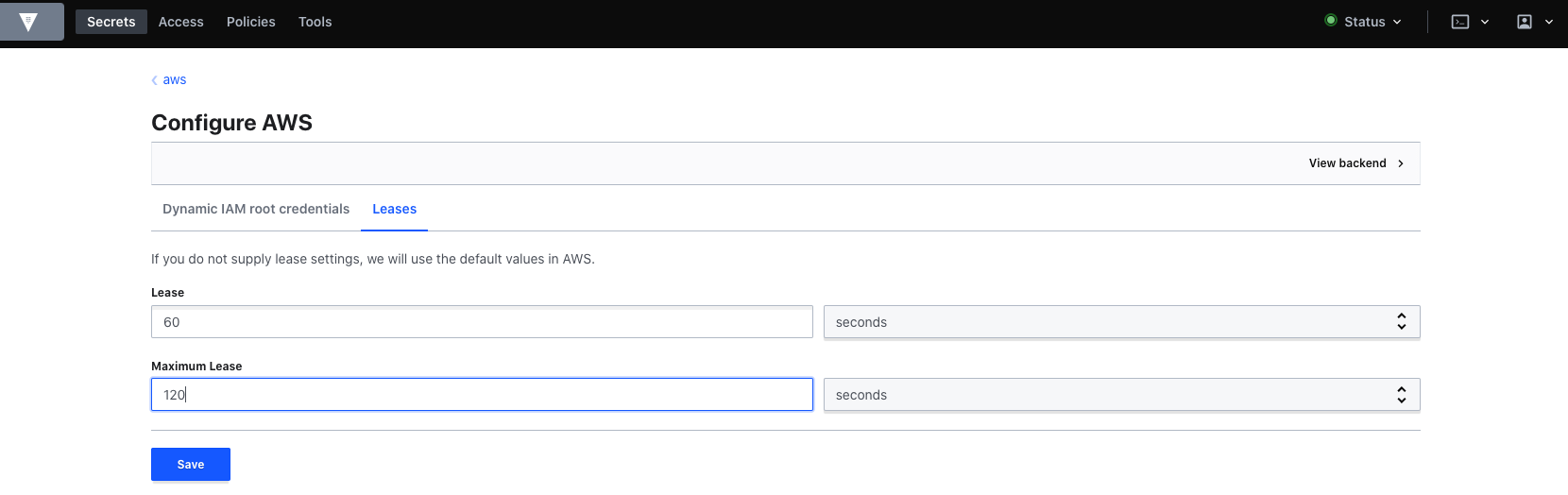
If required, you can also adapt the lease here.
Generate a dynamic secret (AWS credential)
Next we will continue with generating the dynamic secret. This is fairly straightforward:
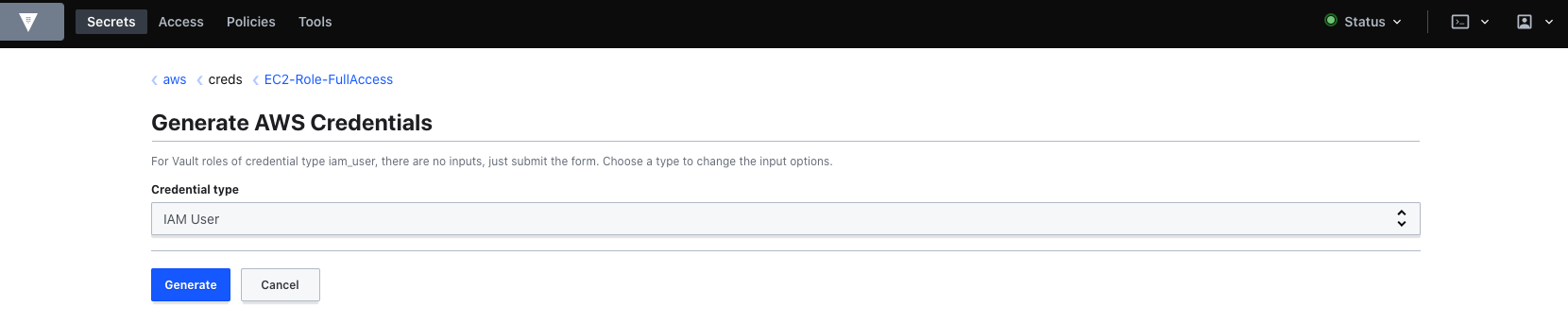
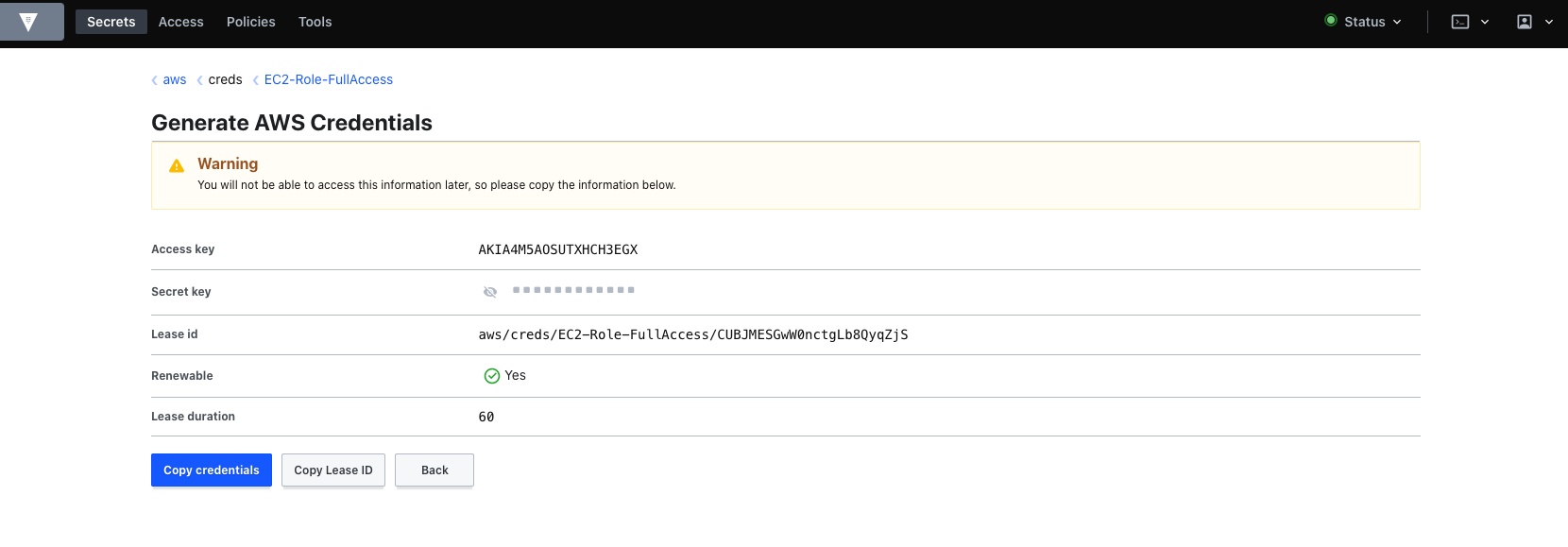
As you can see, Vault will generate these credentials on AWS.
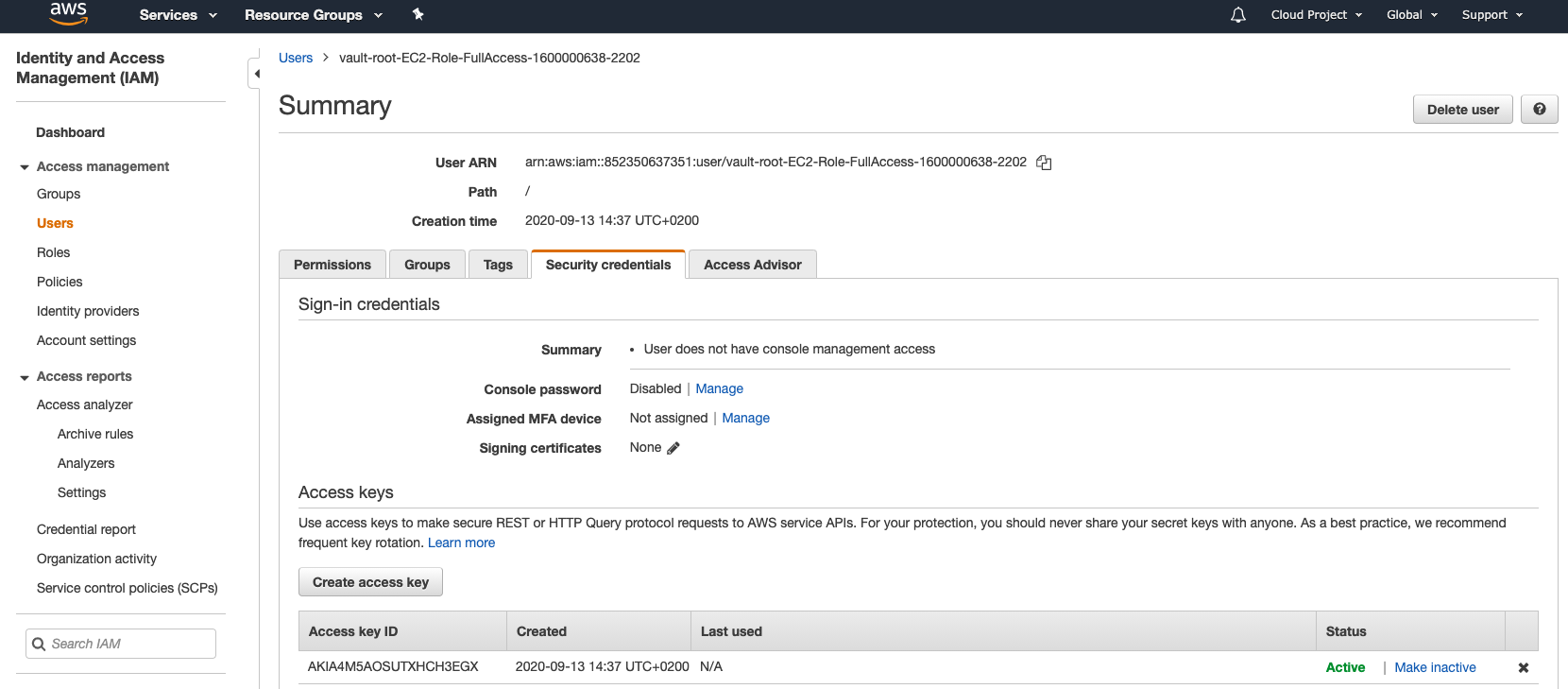
If we go back to the AWS dashboard, you can also see these credentials there.
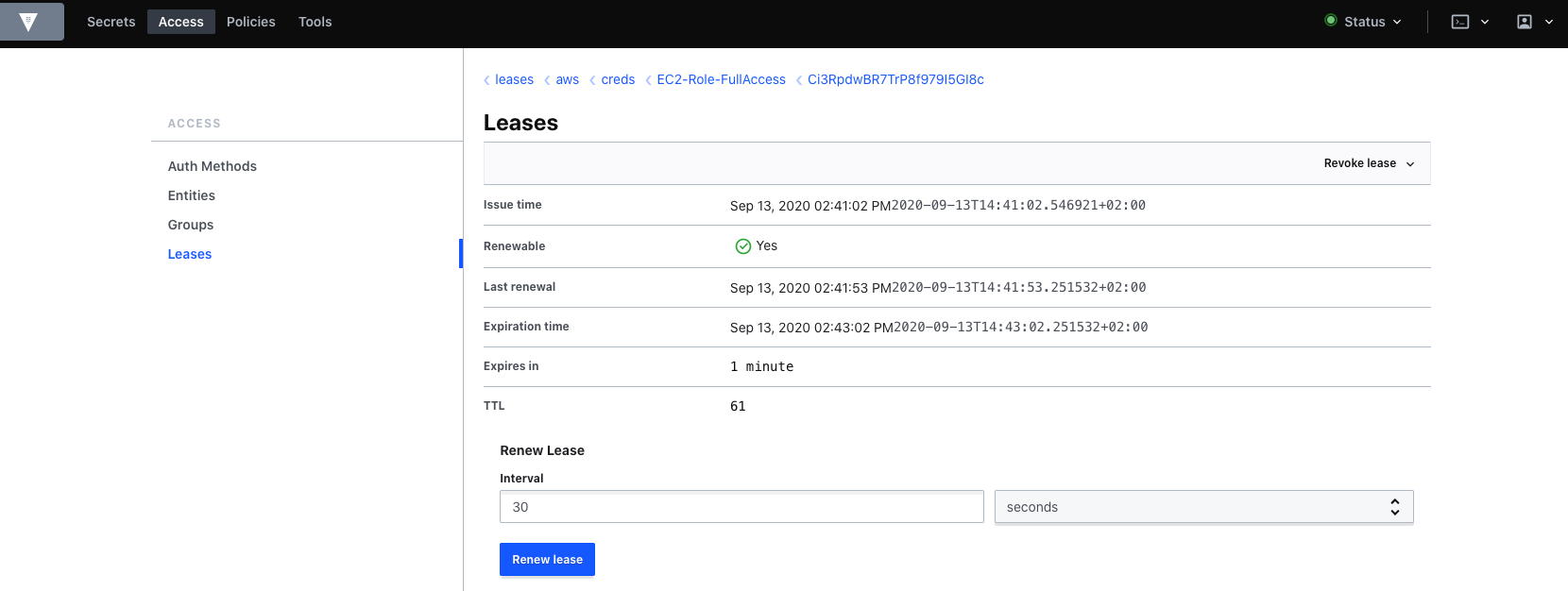
Renew lease
Vault can also renew the lease of the AWS secret.
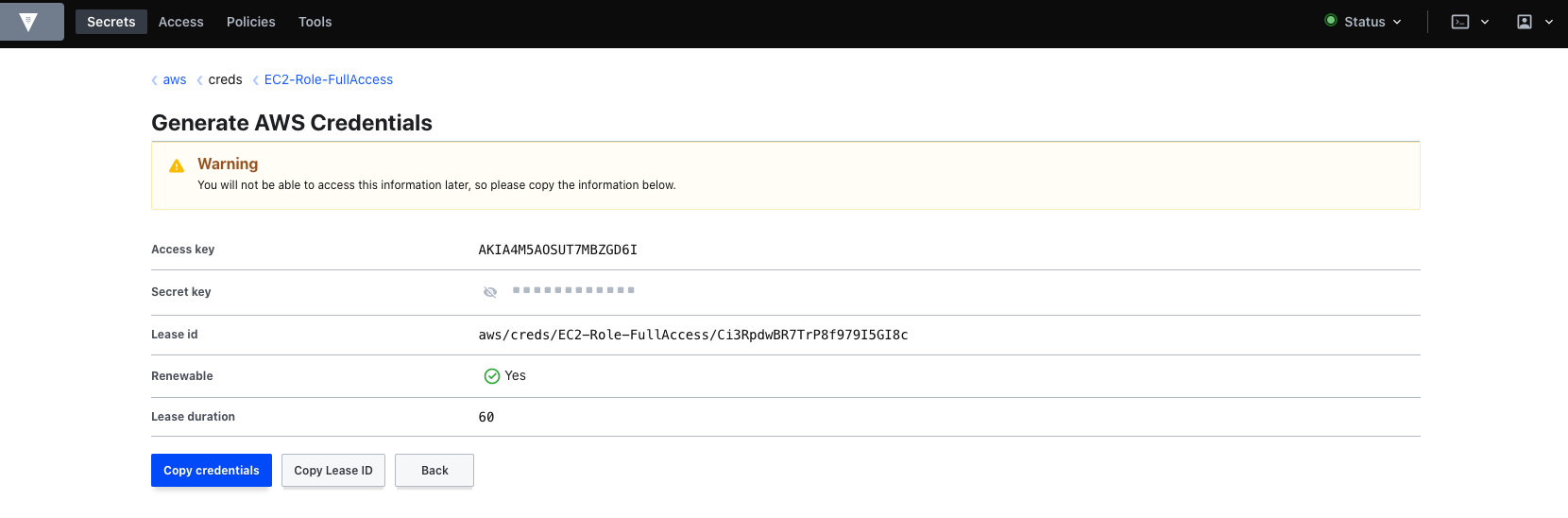
In below screenshot, we have a remaining TTL of 16. So before it expires, we will renew the lease.
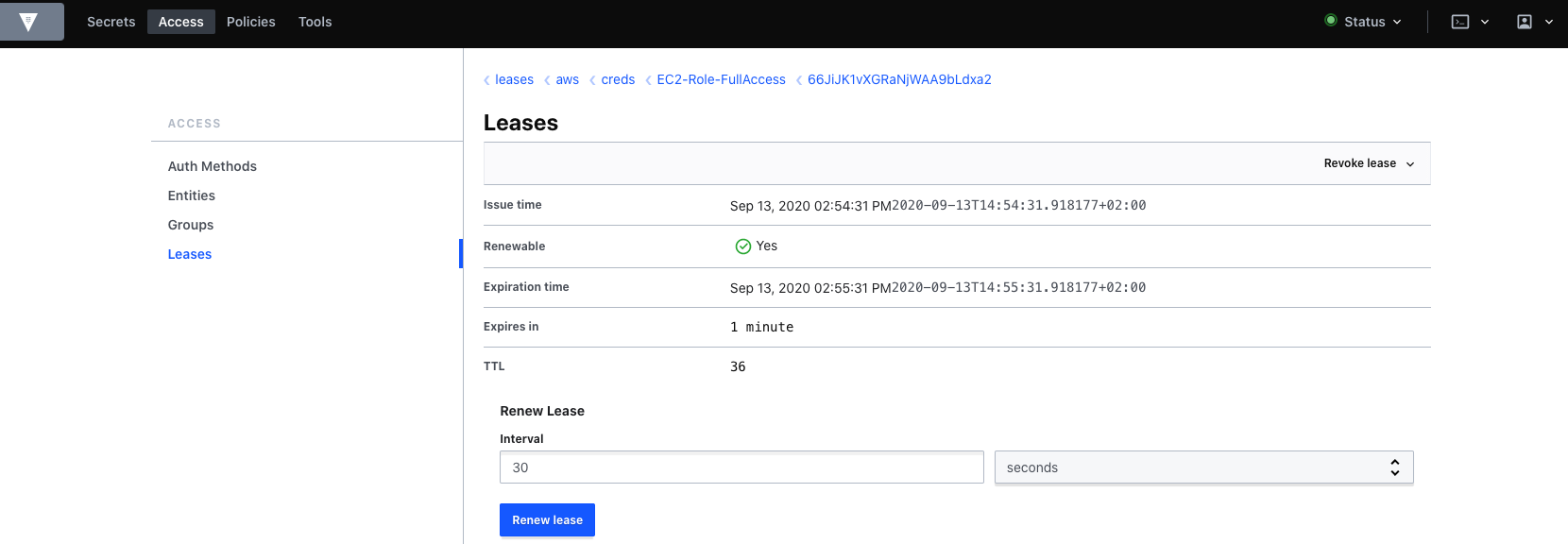
Revoke lease
Obviously we can also revoke the lease. The lease revoke command revokes the lease on a secret and will invalidate the underlying secret.
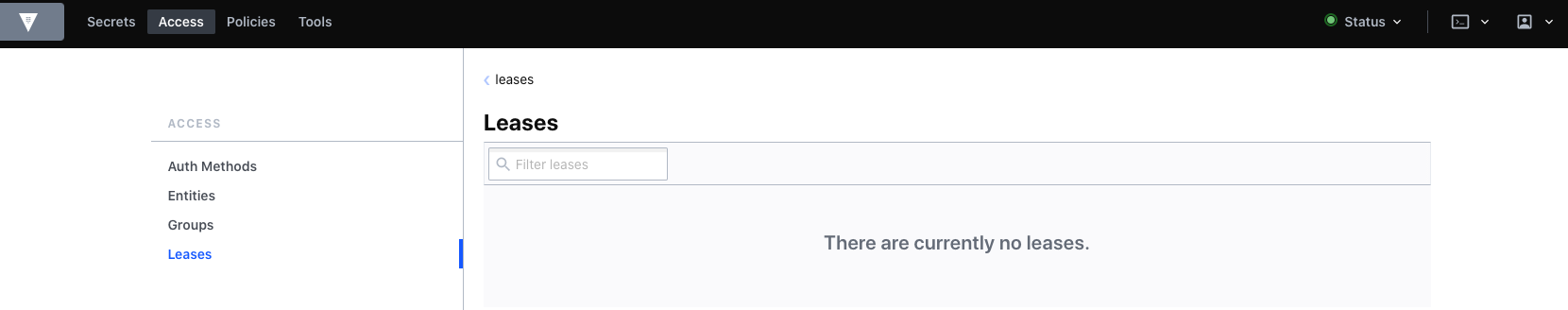
As you can see Vault will not show the secret any longer and it will also be removed from AWS dynamically.
Hope this was a bit helpful. See you next time.
